04.19.23 By Bridgenext Think Tank

HITRUST compliance can deliver undisputed data security, compliance, faster GTM and more! Read on to explore!
Health Information Trust Alliance (HITRUST) was founded in 2007 as a partnership of leaders in healthcare, technology, and information security. Its goal was to develop a unified cyber defense framework for the entire healthcare supply chain. Today, HITRUST offers data protection standards and certification programs which help organizations safeguard sensitive information, handle high levels of data security, and achieve compliance objectives.
HITRUST CSF (Common Security Framework) is the foundation for all services and programs. CSF entails a rigorous assessment procedure, including a third-party audit to assure an organization’s clients, partners, and regulators that it has robust security and privacy controls in place.
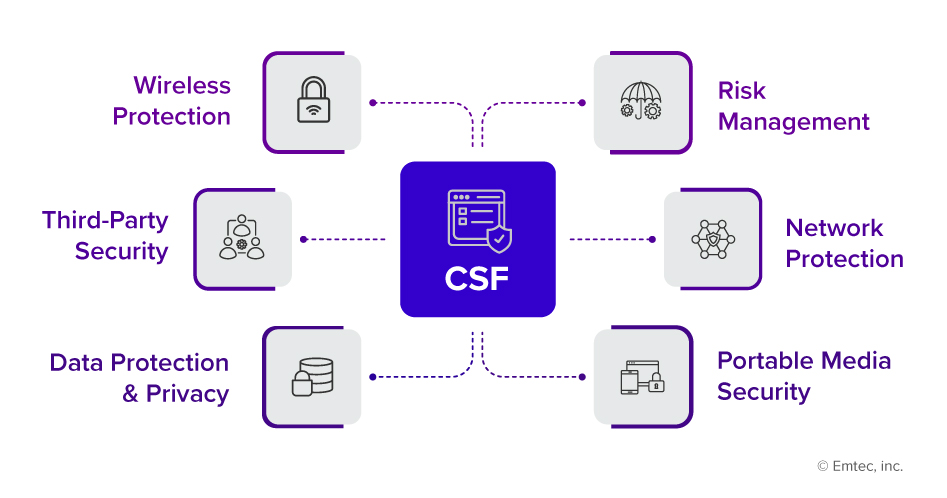
Let’s learn what domains are covered by HITRUST CSF:
There have been 2,100 hospital data breaches in the US over the last ten years. – Astra Security
This surprising statistic shows the high risk of malicious attacks that healthcare organizations face. An organization’s security policies and processes will determine the likelihood of an attack actually succeeding.
In any business, preventing data breaches necessitates a complex combination of microtasks. These can include everything from network patching to updating security policies. However, an organized risk management program at the macro level is critical to ensure comprehensive data security. HITRUST aids healthcare organizations in preventing data breaches by providing guidance on how to implement the appropriate policies, and procedures, and enhance them over time.
The average cost of a data breach in 2021 was $4.24 million per incident, up 10% from the previous year.
Also, the cost per lost or stolen record containing sensitive and confidential information increased from $150 in 2020 to $174 in 2021. – IBM Security
Security frameworks like HITRUST simplify the process for organizations to achieve stringent compliance to guarantee safety of sensitive data. The scope of HITRUST continues to grow with firms in additional industries implementing HITRUST to manage information security risks and protect sensitive data. Here are some examples use cases for a few different industries:
HITRUST can help insurance organizations implement a comprehensive security and compliance program that addresses these challenges and helps them meet regulatory requirements such as the National Association of Insurance Commissioners (NAIC) model law on cybersecurity.
HITRUST is quickly gaining popularity in a wide range of industries to manage information security risk and protect sensitive data.
With so much at stake, what are the benefits of utilizing the HITRUST framework? Let’s discuss the top 4 benefits of using HITRUST now:
People often get confused between the HITRUST and HIPAA frameworks. For better understanding, we have drawn a comparison between both:
| Parameters | HITRUST | HIPAA |
| Definition | A framework developed by industry experts to manage information security risks within organizations. | Federal law that sets the standard for protecting sensitive patient data. |
| Purpose | Provides a more rigorous set of controls that can help organizations manage their overall information security risk more effectively. | HIPAA provides a set of regulations to protect the privacy and security of individually identifiable health information. |
| Scope | HITRUST covers a broad range of security and privacy controls across various industries, including HIPAA. | HIPAA primarily applies to covered entities, such as healthcare providers, health plans, and clearinghouses, and their business associates. |
| Framework | HITRUST CSF incorporates various industry regulations and standards, including HIPAA, NIST, PCI DSS, and others, into a single, comprehensive framework. | HIPAA Security Rule requires covered entities to implement certain administrative, physical, and technical safeguards to protect PHI. |
| Compliance Requirements | HITRUST includes multiple security and privacy regulations, including HIPAA, and requires organizations to implement controls across 19 domains. | HIPAA requires covered entities to implement specific administrative, physical, and technical safeguards to protect PHI. |
| Penalties for Non-Compliance | HITRUST does not have specific penalties for non-compliance, but non-compliance can impact an organization’s ability to do business with partners and customers. | HIPAA violations can result in significant fines and penalties, ranging from $100 to $50,000 per violation, depending on the severity of the violation. |
HIPAA and HITRUST share a common goal of protecting sensitive health information, but HITRUST has an edge over HIPAA in providing a comprehensive and standardized approach to managing information security risks.
Some business challenges that HITRUST can help solve include:
For example:
Financial institutions use the HITRUST framework to comply with regulatory requirements such as the New York Department of Financial Services (NYDFS). This regulation requires banks, insurance companies, and other financial services companies to implement and maintain cybersecurity programs that include risk assessments, written policies and procedures, and employee training.
By using the HITRUST framework and associated apps, financial institutions can identify and remediate security risks, improve their security posture, and demonstrate compliance with regulatory requirements.
| Pros | Cons |
| Comprehensive Framework
HITRUST provides a comprehensive approach to managing and securing sensitive data, covering a wide range of information security and privacy requirements. |
Cost
HITRUST implementation can be costly, particularly for smaller organizations with limited budgets. The implementation process requires significant resources, including time, personnel, and technology. |
| Third-Party Validation
HITRUST certification provides third-party validation that an organization has implemented effective security controls and safeguards. This certification can help demonstrate to customers, partners, and regulators that the organization takes data security seriously and is committed to protecting sensitive information. |
Time-Consuming
Implementing HITRUST can be a time-consuming process as it requires changing existing business processes and workflows. Depending on the size and complexity of the organization, the process can take months to complete. The framework consists of numerous domains, each with multiple control objectives, and implementation requirements. Each domain requires extensive documentation, assessment, and testing, which can be time-consuming. |
| Increased Security and Reliability
HITRUST provides a comprehensive approach to managing and securing sensitive data, covering a wide range of information security and privacy requirements. |
The short answer to why organizations should adopt HITRUST is because it is comprehensive, highly reliable, and rigorous.
As digital information technology becomes increasingly common, organizations are increasingly vulnerable to cyberattacks and breaches. Any organization that needs to address compliance and risk management can benefit from achieving HITRUST compliance. Have a look at few of the reasons to adopt HITRUST:
This is a frequently asked question by small and medium-sized enterprises. How much does it cost? It is a significant and valid concern.
But if we see HITRUST as a medium- to long-term investment, and an ongoing process of improvement rather than a one-time expense, you gain a different perspective. Instead of inquiring how much the HITRUST framework will cost, ask “what will we gain in return for our investment?”
Investing in a robust, comprehensive risk management program is necessary to achieve HITRUST compliance. It requires the creation of solid policies and procedures and their effective implementation. It also involves eliminating the duplication of fundamental steps mandated by multiple regulatory standards. It necessitates the need to collaborate with competent, and well-trained evaluators.
In today’s fast pacing environment, organizations rely heavily on a solid and agile security posture. Brdgenext can assist you in adopting the HITRUST framework. Whether it’s a first-time implementation, or you are looking to enhance your capabilities, our team of experts will guide you in every step.
Ready to take the next step in your HITRUST compliance journey?
Contact us now to learn how we can guide you through the process in the most cost-optimized manner.
References
www.getastra.com/blog/security-audit/healthcare-data-breach-statistics/
www.ibm.com/downloads/cas/OJDVQGRY
www.rsisecurity.com/compliance-advisory-services/nydfs-23nycrr500/